Mosaic 2.0 and NCSA httpd allow access restriction based on several criteria:
You also need to be running Mosaic for X version 2.0 or later, or another browser known to support HTTP/1.0-based authentication.
fido with password
bones.
Important Note: There is no correspondence between
usernames and passwords on specific Unix systems (e.g. in an
/etc/passwd file) and usernames and passwords in the
authentication schemes we're discussing for use in the Web. As
illustrated in the examples, Web-based authentication uses
similar but wholly distinct password files; a user need
never have an actual account on a given Unix system in order to
be validated for access to files being served from that system
and protected with HTTP-based authentication.
rover with
password bacon and user jumpy with
password kibbles.
ncsa.uiuc.edu.
Note for non-NCSA readers: The .htaccess file
used in this case is as follows:

AuthUserFile /dev/null AuthGroupFile /dev/null AuthName ExampleAllowFromNCSA AuthType Basic <Limit GET> order deny,allow deny from all allow from .ncsa.uiuc.edu </Limit>

ncsa.uiuc.edu.
Note for NCSA readers: The .htaccess file
used in this case is as follows:

AuthUserFile /dev/null AuthGroupFile /dev/null AuthName ExampleDenyFromNCSA AuthType Basic <Limit GET> order allow,deny allow from all deny from .ncsa.uiuc.edu </Limit>

Per-directory authentication means that users with write access to part of the filesystem that is being served can control access to their files as they wish. They need not have root access on the system or write access to the server's primary config files.
Access control for a given directory is controlled by a file named
.htaccess that resides in that directory. The server
reads this file on each access to a document in that directory (or
documents in subdirectories).
turkey to username pumpkin and password
pie. Here's what to do:
 Create a file called
Create a file called
.htaccess in directory turkey that looks
like this:

AuthUserFile /otherdir/.htpasswd AuthGroupFile /dev/null AuthName ByPassword AuthType Basic <Limit GET> require user pumpkin </Limit>

Note that the password file will be in another directory
(/otherdir).
Also note that in this case there is no group file, so we specify
/dev/null (the standard Unix way to say "this file
doesn't exist").
AuthName can be anything you want. AuthType
should always currently be Basic.
 Create the password file
Create the password file
/otherdir/.htpasswd.
The easiest way to do this is to use the htpasswd program
distributed with NCSA httpd. Do this:

htpasswd -c /otherdir/.htpasswd pumpkin

Type the password -- pie -- twice as instructed.
Check the resulting file to get a warm feeling of self-satisfaction; it should look like this:

pumpkin:y1ia3tjWkhCK2

That's all. Now try to access a file in directory turkey
-- Mosaic should demand a username and password, and not give you
access to the file if you don't enter pumpkin and
pie. If you are using a browser that doesn't handle
authentication, you will not be able to access the document at all.
So basically this method of authentication is roughly as safe as
telnet-style username and password security -- if you
trust your machine to be on the Internet, open to attempts to
telnet in by anyone who wants to try, then you have no
reason not to trust this method also.
 Add additional users to the directory's
Add additional users to the directory's
.htpasswd file.
Use the htpasswd command without the -c flag
to additional users; e.g.:

htpasswd /otherdir/.htpasswd peanuts htpasswd /otherdir/.htpasswd almonds htpasswd /otherdir/.htpasswd walnuts

 Create a group file.
Create a group file.
Call it /otherdir/.htgroup and have it look something
like this:

my-users: pumpkin peanuts almonds walnuts

... where pumpkin, peanuts,
almonds, and walnuts are the usernames.
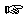 Then modify the
Then modify the .htaccess
file in the directory to look like this:

AuthUserFile /otherdir/.htpasswd AuthGroupFile /otherdir/.htgroup AuthName ByPassword AuthType Basic <Limit GET> require group my-users </Limit>

Note that AuthGroupFile now points to your group file and
that group my-users (rather than individual user
pumpkin) is now required for access.
That's it. Now any user in group my-users can use
his/her individual username and password to gain access to directory
turkey.
CERN has extensive documentation on HTTP-based authentication.
 Return to the
Tutorial Overview
Return to the
Tutorial Overview
NCSA httpd Development Team
httpd@ncsa.uiuc.edu